Table of Contents
Office 365 Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a method of authentication that requires the use of more than one verification method and adds a second layer of security to user sign-ins and transactions. It works by requiring any two or more of the following verification methods.
1. Verification methods
1.1 Authentication phone (SMS)
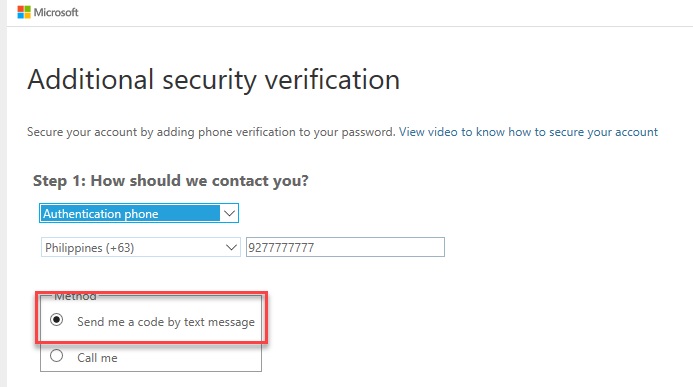
1.1.1 Send me a code by text message
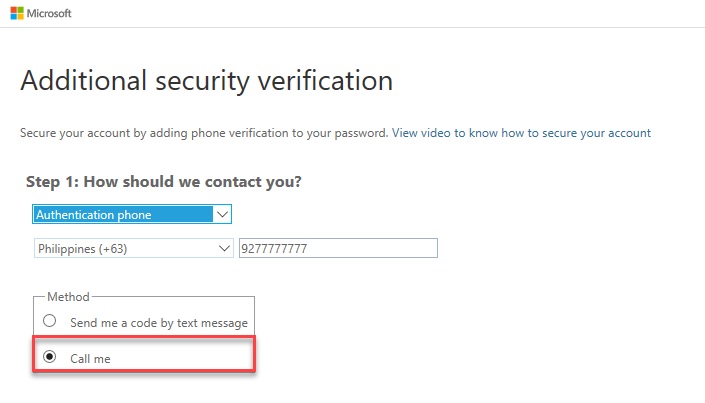
1.1.2 Call Me
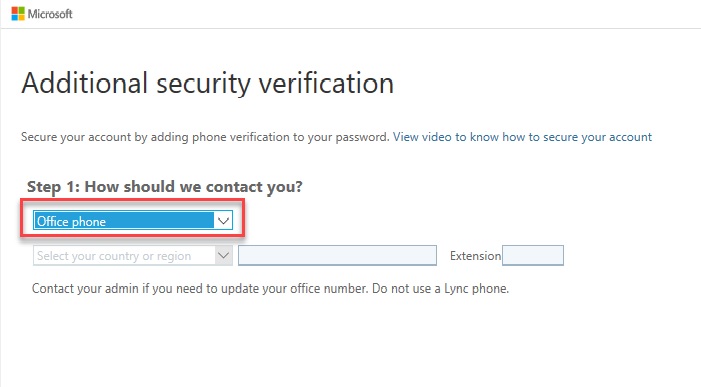
1.2 Office phone call
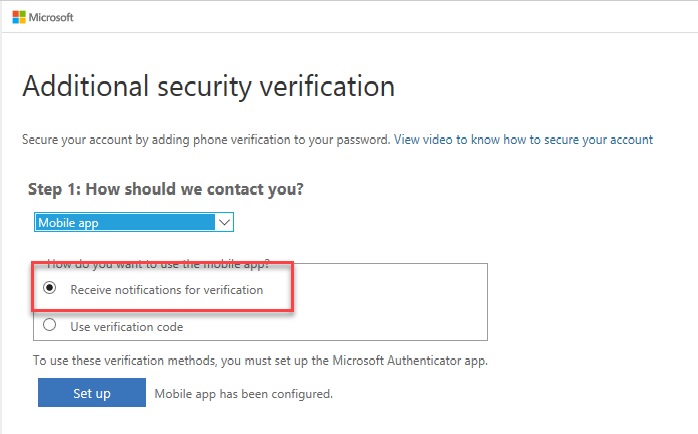
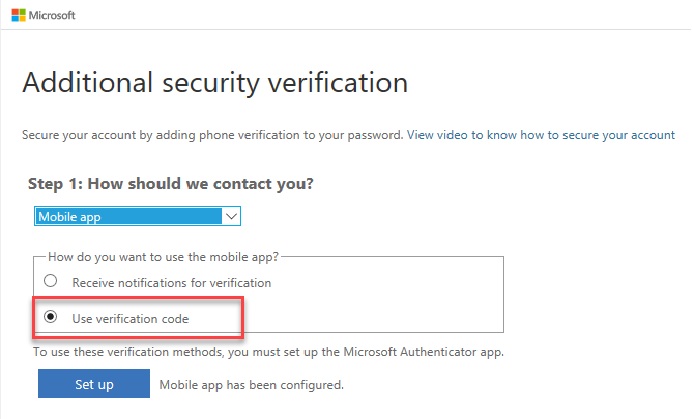
1.3 Mobile app (Notification)
1.3.1 Receive notifications for verification
1.3.2 Use verification code
2. Set up multi-factor authentication in Microsoft 365 admin center
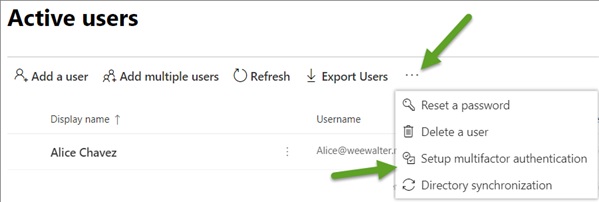
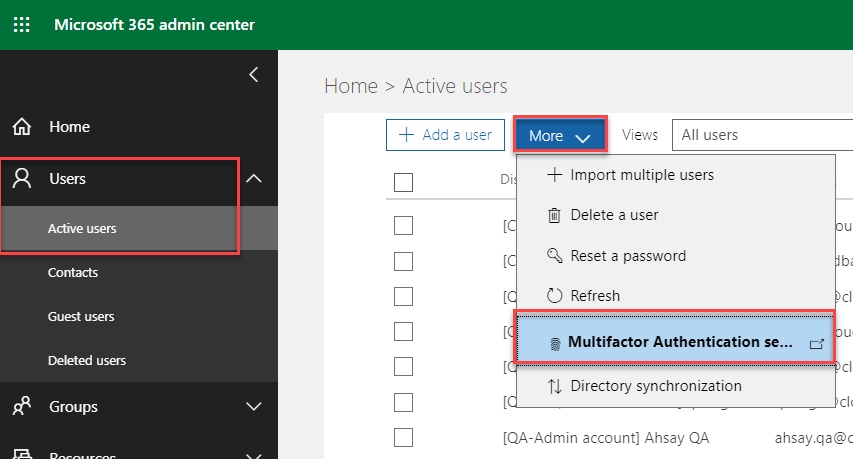
2.1.In the Office 365 Main Menu, click the Admin Center icon, go to Users > Active users.
2.2a. When Using Preview Mode - On the tab Menu, click the triple dot (…) button (after “↓Export Users”) > Setup Multifactor authentication.
2.2b. When Using Classic Mode - On the tab Menu, click “More” Dropdown list (beside “+Add a user”) > Multifactor Authentication setup.
Both Preview and Classic Modes will go to the same link: https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx
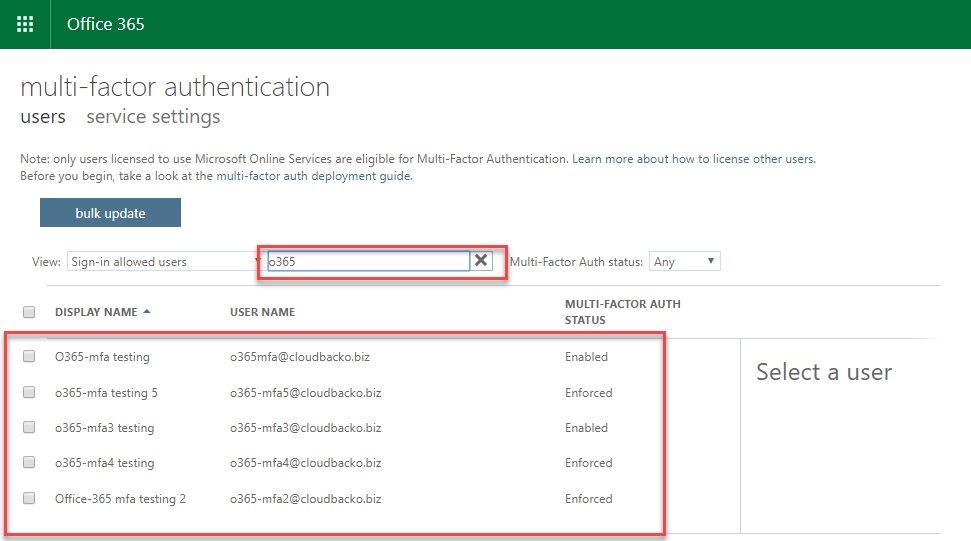
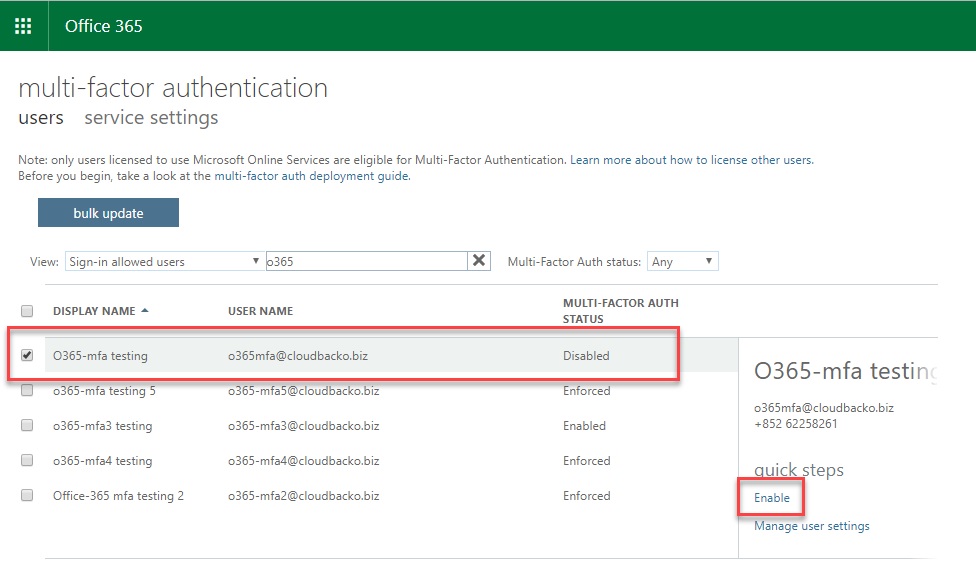
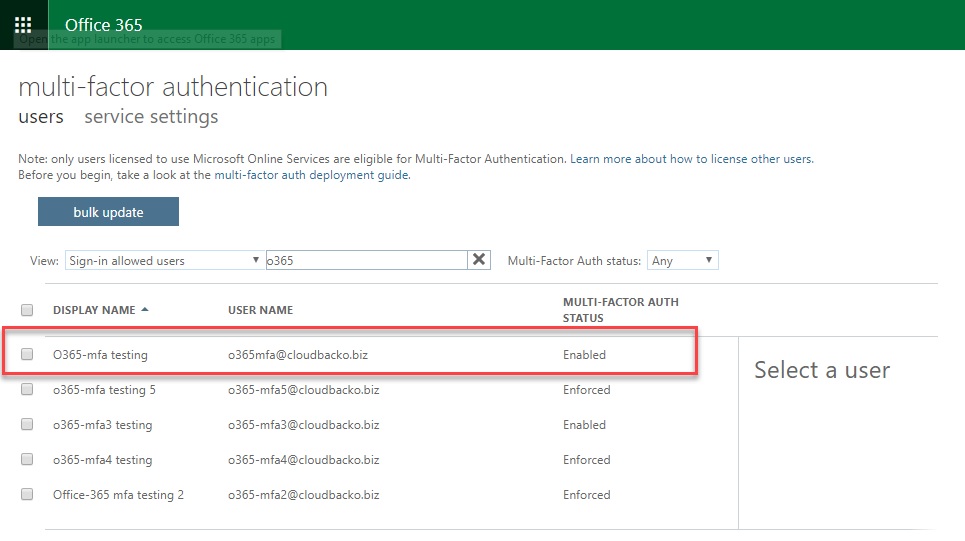
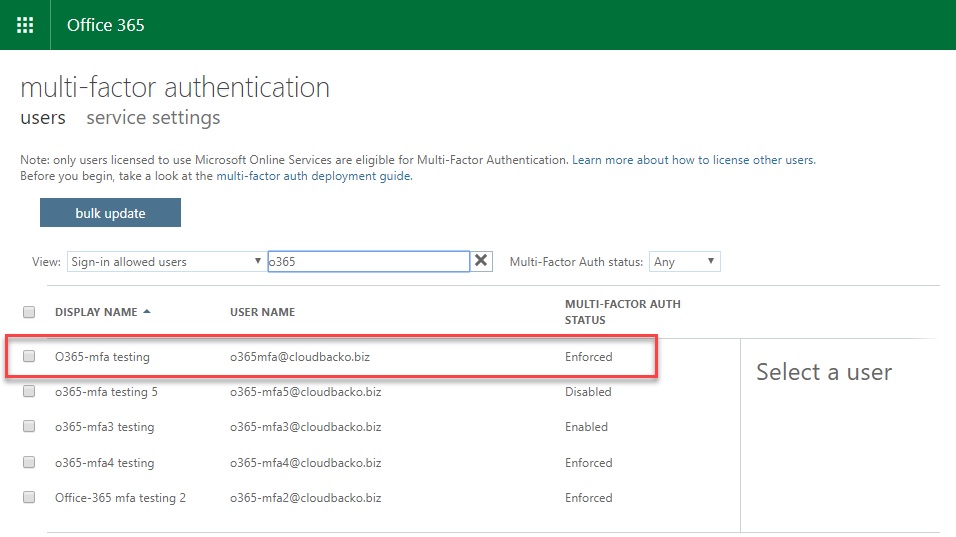
2.3. Search for the account to be used for MFA Setup (Used the given accounts, search for “o365”).
2.4. Click the account that you want to enable MFA.
2.5. There are 3 Multi-factor Auth Status (Disable, Enable and Enforce) can be viewed based on the MFA state of the users.
Disable, Enable and Enforce buttons can be found under the wording “quick steps”.
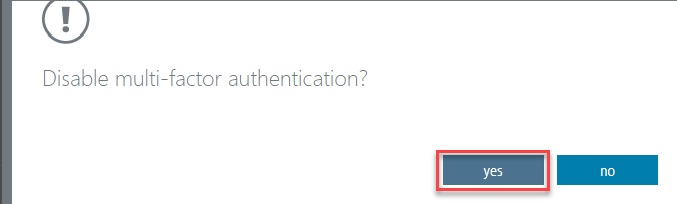
Disabled - This is the default state for any user who is not enrolled in MFA. This means the user is not using MFA and the non-browser apps remain unaffected.
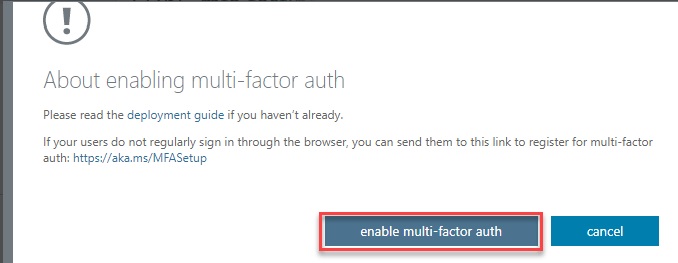
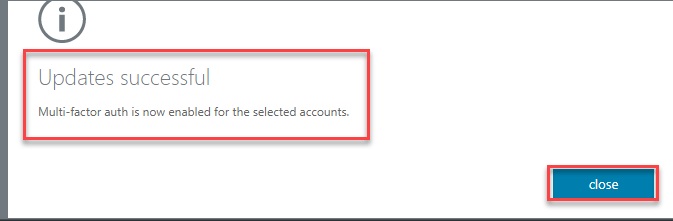
Enabled - In this state, the user is enrolled in MFA, but the changes have not taken effect. When users sign in the next time, they’ll be prompted to set up an additional verification method. Here too, nonbrowser apps remain unaffected until the setup is complete.
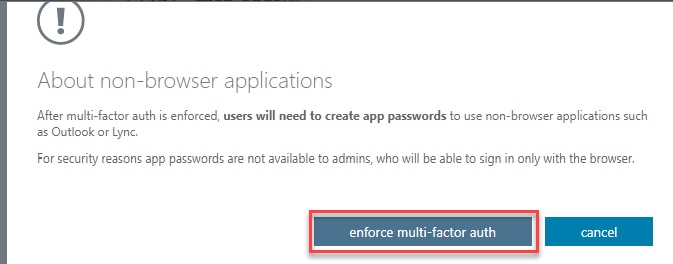
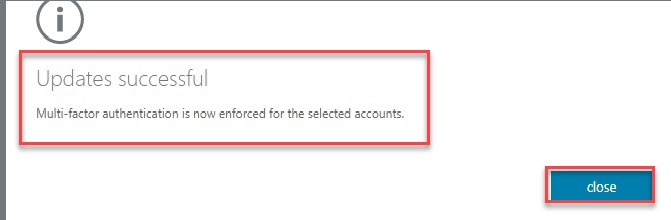
Enforced - User is enrolled in MFA and has completed the registration process. In this state, every login requires a secondary authentication. Non-browser apps will not work until app passwords are created and entered at the time of login.
3. Verification
3.1 Authentication phone (SMS)
3.1.1. Set the Multi-Factor Auth Status of the user/account to Enabled.
3.1.2. Go to OWA site, login the user/account.
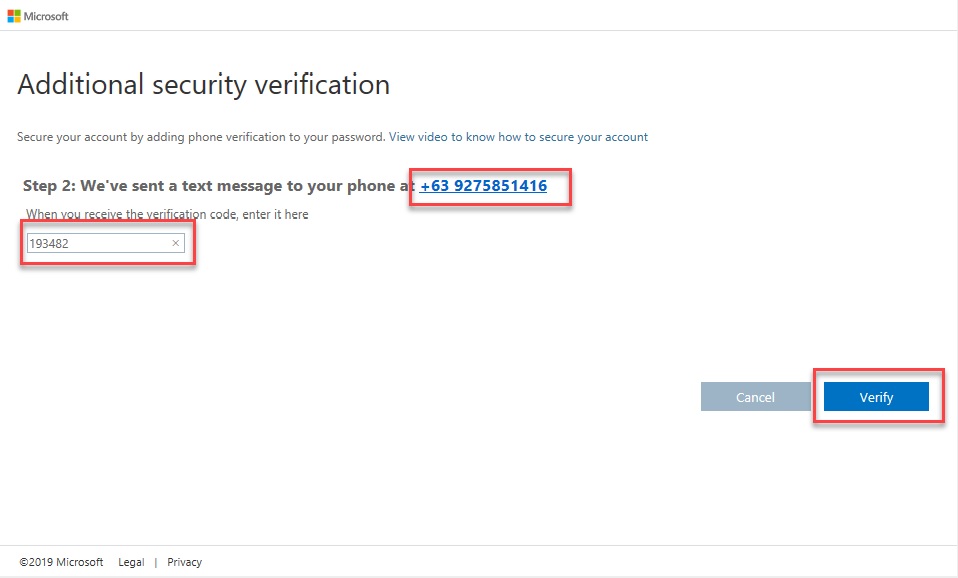
3.1.3. Select “Authentication Phone”, Enter Country or Region, Enter Mobile Phone number.
–. Select “Send me a code by text message” as Method. Click Next Button.
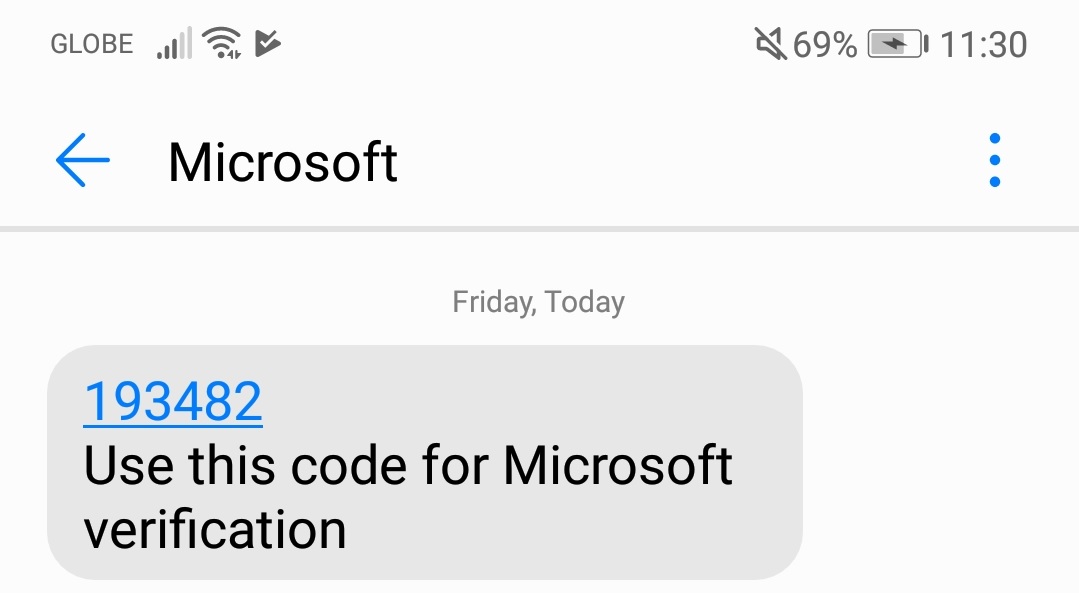
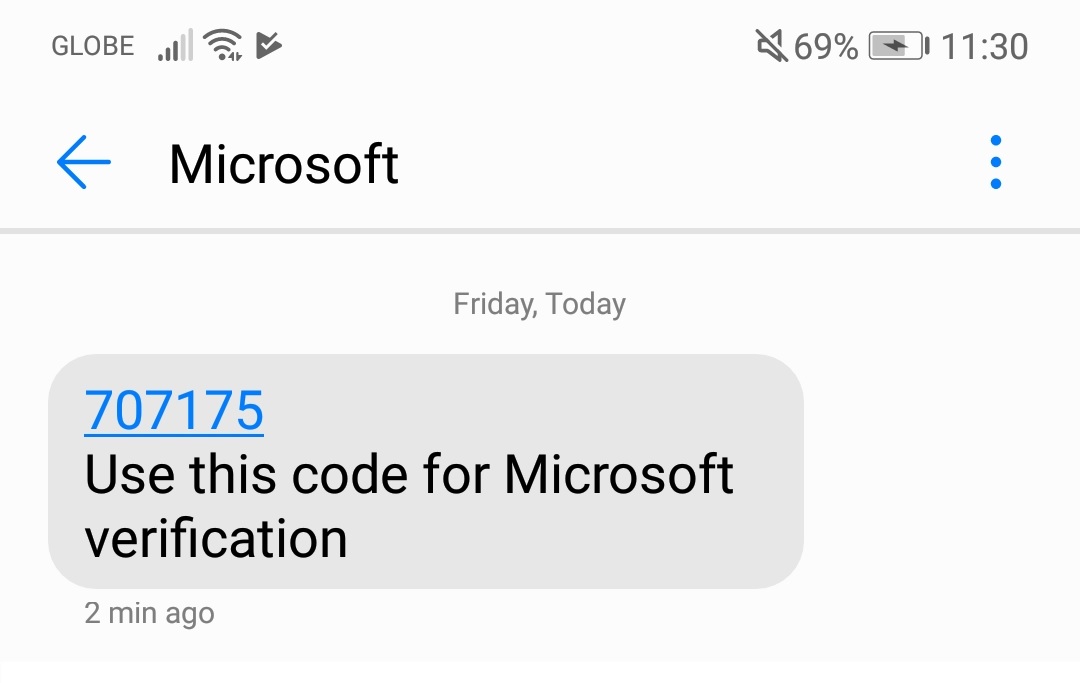
3.1.4. The App will send an SMS for the code and will use for Microsoft verification.
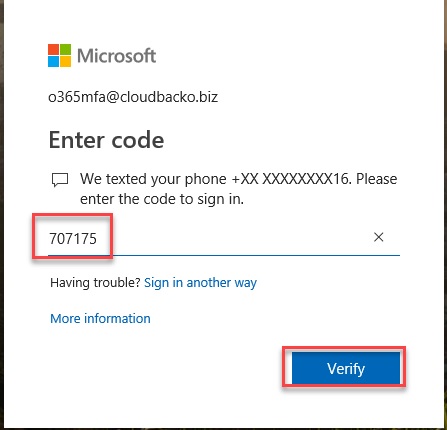
–. Enter Verification code from SMS. Click Verify Button.
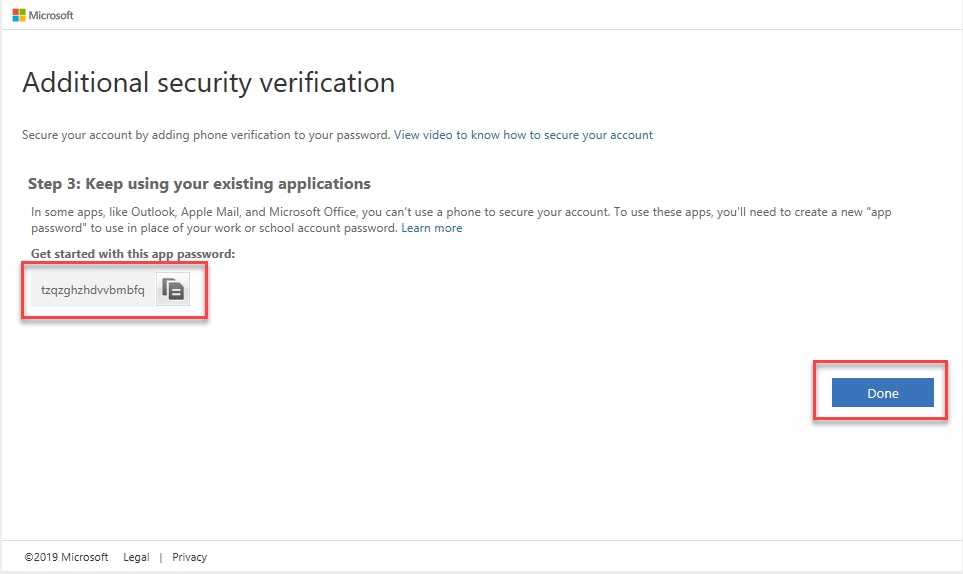
–. Copy the App Password then click Done.
3.1.5. When user will try to re-login, the App will send another SMS having the code for Microsoft verification.
3.1.6. The Multi-Factor Auth Status is now turned to Enforced.
3.2 Authentication phone (Mobile Phone Call)
3.2.1. Set the Multi-Factor Auth Status of the user/account to Enabled.
3.2.2. Go to OWA site, login the user/account.
3.2.3. Select “Authentication Phone”, Enter Country or Region, Enter Mobile Phone number.
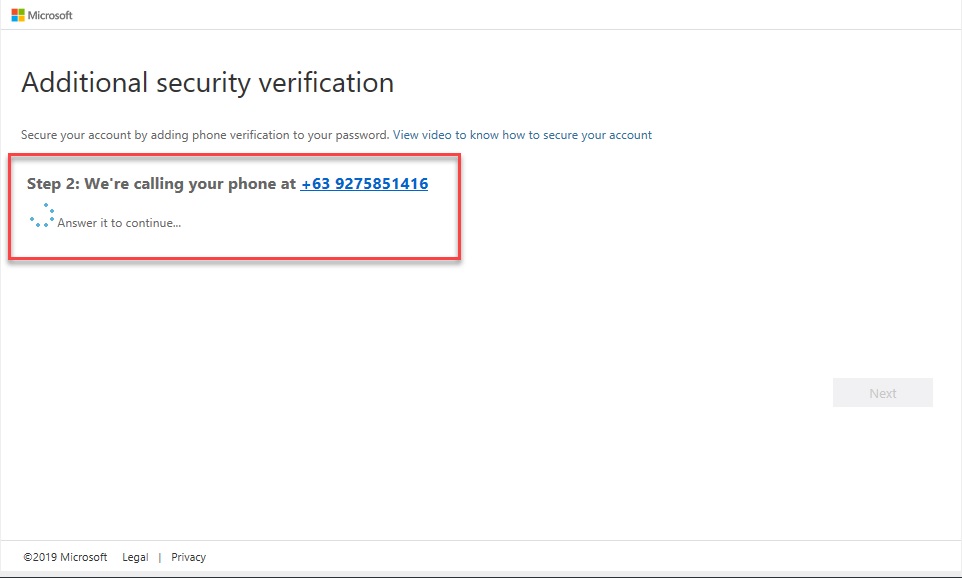
–. Select “Call Me” as Method. Click Next Button.
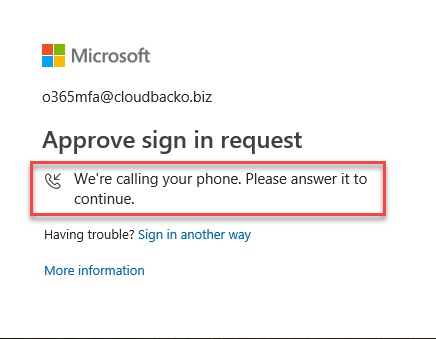
3.2.4. The App will call the mobile number for Microsoft verification.
–. Answer the call then click Pound (#) key.
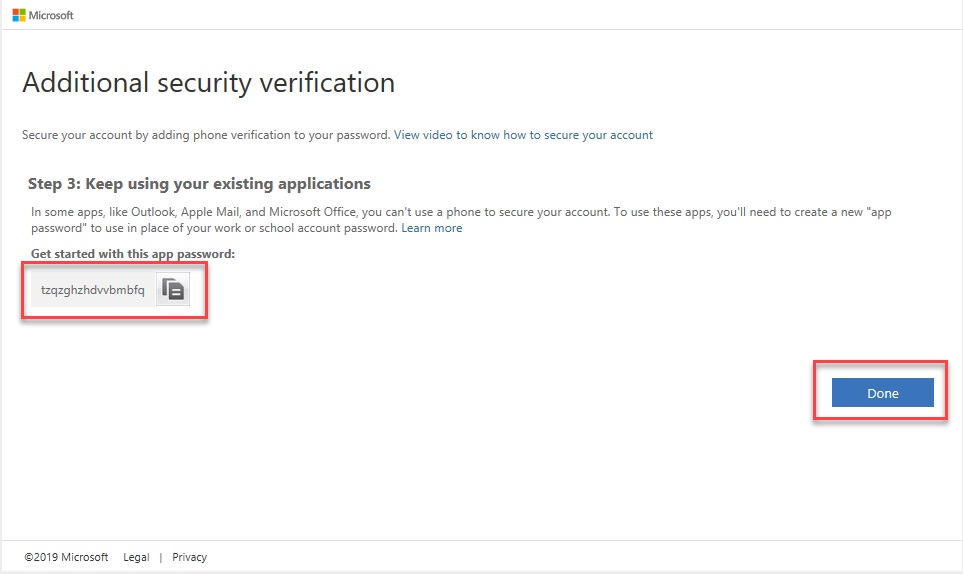
–. Copy the App Password then click Done.
3.2.5. When user will try to re-login, the App will call the mobile phone again for Microsoft verification.
3.2.6. The Multi-Factor Auth Status is now turned to Enforced.
4. Notes
4.1 Office 365 settings changes would NOT immediately reflect in CloudBacko
- This is known during testing. The settings changed in Office 365 would NOT immediately take effect (This is a limitation in Microsoft). For example, the change of MFA status, App Password etc. in Office 365 needs some time to take effective. This is very uncommon in real life scenario that the settings in Office 365 were changed and customers immediately work with Office 365 backup sets in CloudBacko.
- False alarm could be raised if unexpected behaviour were seen in CloudBacko after settings in Office 365 changes and not yet take effective. Please retry after the settings changed in Office 365 took effective.